No products in the cart.
Blog
3 Common SIM Card Hacks and How To Avoid Them
Hardware and software innovation has given us exceptional new user experiences. We can make online payments, send texts and emails, browse the internet, and more. And we can do it all from our smartphones.
New technology may make our lives easier, but it also increases the risk of our data getting into the wrong hands. Data security is constantly at odds with hackers, scammers, and other identity theft professionals. And with so much sensitive information on our devices, we’ve got to be on the lookout.
Here, we’ll cover the most common SIM card hacks, how to avoid them, and why an eSIM could be a safer option.
Why SIM Cards Get Hacked
First, let’s review why SIM cards get hacked in the first place. One of the most important things linked to your phone number is access to two-factor authentication (2FA). If a scammer can hack those verification texts, they can:
- Access personal and private data
- Access your contact list
- Track and send calls and texts
- Access email and social media accounts
- Access online banking and credit card credentials
With this type of access, a scammer can easily impersonate you, steal your identity, run scams on your friends and family, and more.
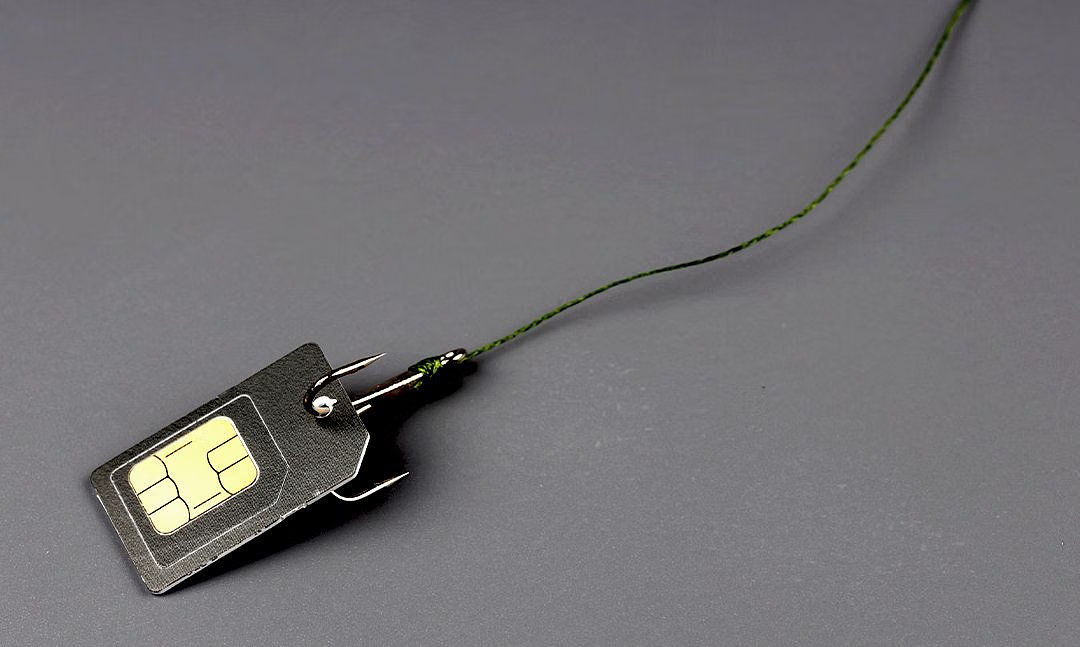
The Most Common SIM Card Hacks
SIM-Jacking
SIM-jacking is when a hacker sends an SMS to gain access to your calls and text messages. Typically, the SMS includes a link instructing your SIM to give the hacker access to your calls, texts, and geolocation.
From your SMS messages, the hacker can access your apps and passwords using 2FA credentials. This puts any account connected to your phone number at risk, including your email, bank account, e-commerce logins, and more.
The best way to protect yourself against SIM-jacking is to be extra wary of links sent by sources you don’t recognize or can’t verify. In general, beware of anyone claiming to represent:
- Financial services
- Credit fraud
- License numbers of license plate verification
- Health information
- Government agents
Reputable sources will contact you through appropriate channels — they won’t send you an SMS. If you receive a text notification like this, it’s best to delete it.

SIM Swapping
SIM swapping is a security breach where the hacker will pretend to be you and commit fraud on your behalf. Typically, they’ll start by gathering information about your financial history, user records, security questions, payment cards, and phone numbers.
Then, they’ll call your cellular provider, pretend to be you, and claim your SIM card was lost or stolen. They’ll provide the necessary personal and financial information to prove their identity, and the provider will issue them a new SIM card.
From there, two things will happen. First, your actual SIM will be deactivated and stop working. Second, the hacker will have full access to your data plan, phone number, stored credit cards, saved passwords, and any 2FA requests sent to your phone.
Identity theft is a serious crime and is difficult to stop once it’s happened. The best way to prevent your personal information from being compromised is to be extra careful online and periodically change your passwords. Be aware of where you input sensitive data, whether your network is secure, and if you’re running virus protection software.

SIM Cloning
SIM cloning is a more direct approach whereby hackers take your SIM card, copy the information to a blank SIM, and pretend to be you. This type of unauthorized access is trickier for a scammer to pull off, as they need to get their hands on your physical SIM.
The types of individuals typically targeted by these attacks are those with access to trade secrets or sensitive information, like company executives or government officials. It’s unlikely you’d be a target as a regular citizen.
However, it’s still important to keep track of your SIM card. If it isn’t in your phone (e.g., you’re traveling abroad and swapped it out for a local SIM), store it somewhere safe and out of reach. And make sure you keep your phone on you at all times.

How to Avoid Getting Hacked
Luckily, there are a few ways to keep your SIM card secure and avoid getting hacked. Let’s get into it.
1. Watch Out for Suspicious Texts
Watch out for suspicious texts, calls, or emails. Don’t give sensitive information (e.g., PIN, passwords, security codes) to a third party. It’s unlikely that your bank, credit card provider, or mobile carrier would ask for this information online or over the phone.
2. Switch Up Your Passwords
We know having multiple passwords is a hassle. Still, it’s a good idea if you want to keep your data and personal information secure. Use a different password for everything, and be mindful of where you store your passwords (e.g., don’t keep a list in your Notes app). Luckily, plenty of password manager apps can help you keep track!
3. Keep Track of Your SIM Card
Treat your SIM card like a physical credit card. Be aware of who you buy it from and where you store it when you travel. Choose a reputable SIM vendor (you want to avoid accidentally purchasing a cloned SIM) or ask your cellular provider to issue you a travel SIM.
Once you have a SIM card you can trust, be sure to safely store your SIM(s) while traveling. This is especially true if you have multiple chips for multiple locations. Find ways to minimize the number of SIM cards you carry at a time, as it only takes one compromised card for a security breach to happen.

Is an eSIM More Secure?
Since an eSIM is embedded in your device, it has a “built-in” layer of security. A hacker can’t clone an eSIM or claim it’s been lost since it can’t be physically removed from your device. In this sense, an eSIM is less vulnerable to SIM swapping and cloning scams.
However, all things digital are at risk of being hacked, and an eSIM is no exception. The same general tips apply:
- Look out for suspicious texts, calls, and emails.
- Don’t open links from unverified sources.
- Switch up your passwords periodically.
- Keep your personal information private.
Whether you have a SIM or an eSIM, it’s a good idea to be aware of potential security threats and how to avoid them.
Want to learn more about eSIM technology? Check out our latest articles on the Airalo blog.

